Advances in Cloud technologies and AI come with a down side: the attack surface for bad actors in cybersecurity continues to expand. With the regulatory environment in constant flux, achieving cyber resilience at an enterprise level is essential.
Awareness of the challenges is present, yet significant gaps persist. To safeguard their organisations, executives must treat cybersecurity as a crucial standing item on the business agenda. A cybersecurity perspective needs to be embedded in every strategic decision at C-Level.
Significant gaps in preparedness
77 countries, 4,042 business and tech executives, one survey: PwC’s 2025 Global Digital Trust Insights highlight significant gaps companies must bridge now to secure a necessary level of cyber resilience.
- Gaps in implementation of cyber resilience: Despite heightened concerns about cyber risk, only 2% of executives report active cyber resilience measures across their organisation.
- Gaps in preparedness: Paradoxically, many feel least prepared to address the cyber threats they find most concerning, such as cloud-related risks and third-party breaches.
- Gaps in CISO involvement: Less than half say their CISOs are involved to a large extent with strategic planning and tech deployments.
- Gaps in regulatory compliance confidence: CEOs and CISOs/CSOs have differing levels of confidence in their ability to comply with regulations, particularly regarding AI, resilience and critical infrastructure.
- Gaps in measuring cyber risk: Although executives acknowledge the importance of measuring cyber risk, fewer than half do so effectively. Only 15% measure the financial impact of cyber risks to a significant extent.
Takeaway:
This points to the need for better C-suite collaboration and strategic investment to strengthen cyber resilience. There is no alternative to addressing these gaps and making cybersecurity a business priority. CISOs can help drive this outcome by sharing tech-enabled insights and by explaining cyber priorities in business terms (cost, opportunity, risk).

A shared vision for preparedness
In the evolving cybersecurity landscape, threats are increasingly volatile and unpredictable. Cloud, AI, and connected services as well as integration of third parties create an expanding attack surface. This situation demands an agile, enterprise-wide approach to cyber resilience. Aligning organisational priorities and readiness is essential for maintaining security and business continuity.
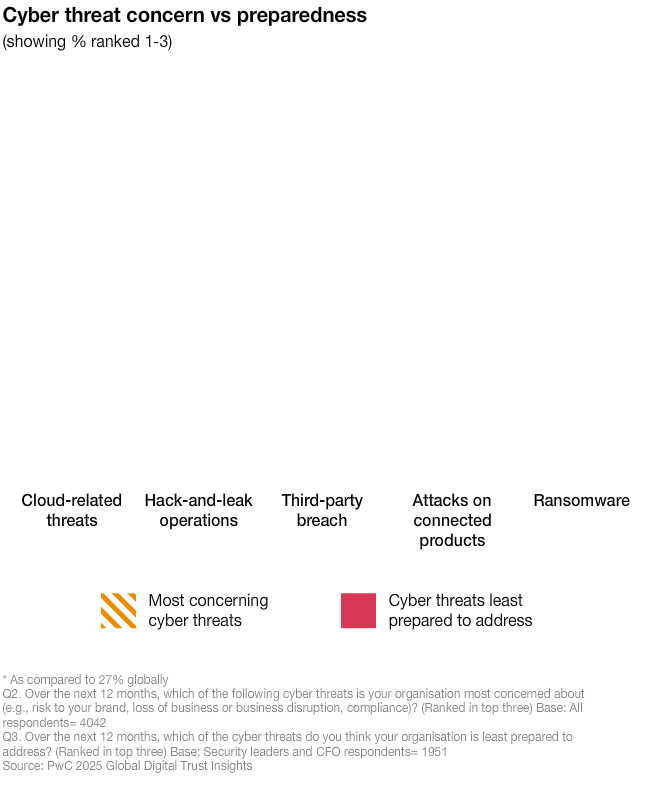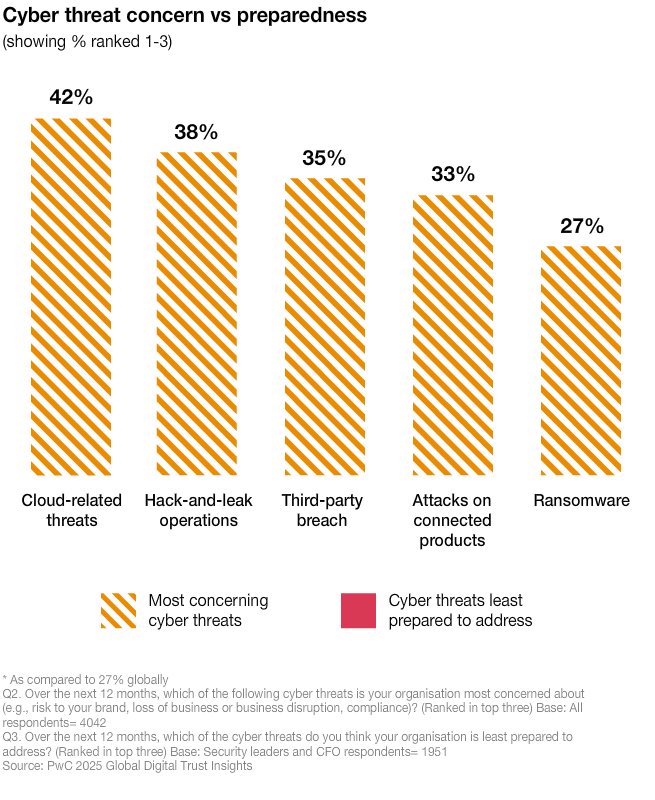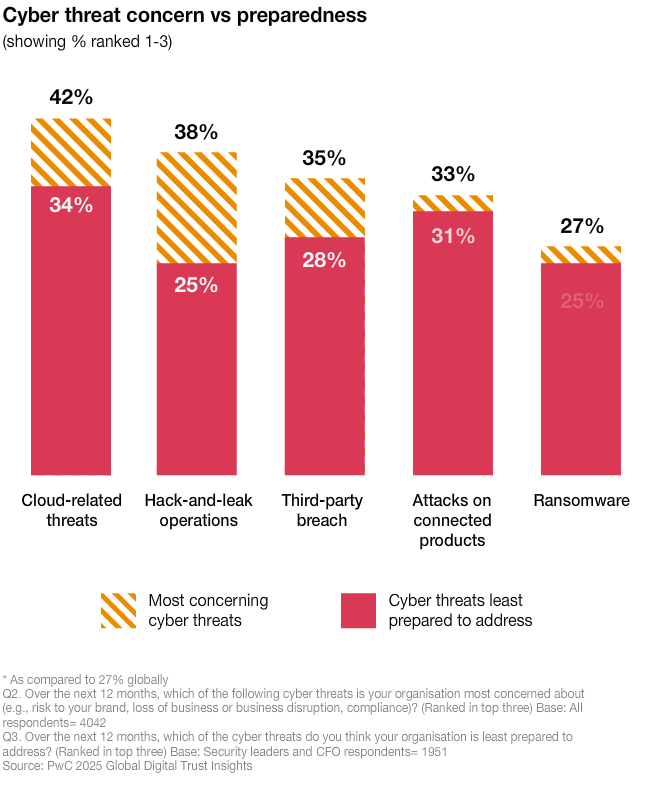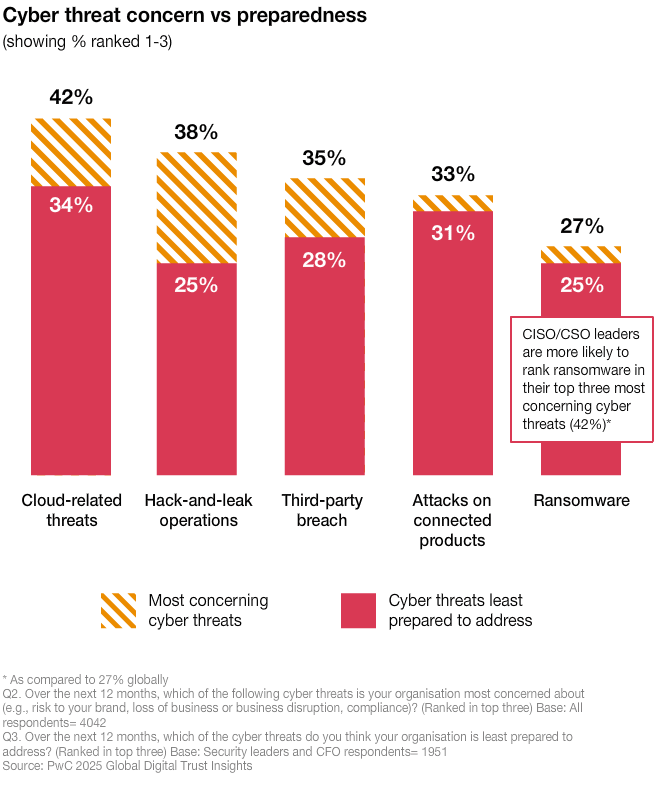
Unprepared for the most concerning threats
The greatest worries are issues organisations are least prepared for. These are the top four cyber threats:
- cloud-related threats
- hack-and-leak operations
- third-party breach
- attacks on connected products
The same threats are listed as those security leaders feel least prepared to address. This gap highlights the urgent need for better investments and stronger response capabilities.
Executive call-to-action
Underscore to the rest of the C-suite the threats that jeopardise the business most, especially if investment efforts need to be shifted.
Based on conversations with the risk executives, gauge how certain threats can damage information and infrastructure security at large and which threats pose the biggest challenge to resilience.
Gain deeper insight from the CISO and CRO on the most critical cyber management and investment priorities.
Meet regularly with the CRO and CISO to understand the threat vectors they’re most concerned about. Make sure you’re receiving regular reporting on current threat mitigation efforts.
Understand the top cyber risks to the organisation and ask the tough questions of management. How are risks being mitigated? Do we have adequate plans and funding in place to proactively address risks and respond should an event occur?

Balancing opportunity and risk
While the rapid advancement of generative AI (GenAI) is ushering in new opportunities across industries, it also presents new cybersecurity risks. GenAI and other emerging technologies challenge leaders to navigate increasingly complex and unpredictable attack vectors, integration challenges and the fact that GenAI features strongly on both sides of the divide: in cyber defence and cyber offence.
Leveraging GenAI for cyber defence: Opportunities and challenges
The top three ways of leveraging GenAI in cybersecurity and defence against cyber threats include threat detection and response, threat intelligence and malware/phishing detection.
Executive call-to-action
Help to drive standardisation across the technology estate to help integrate AI. Enforce access rights on a user-by-user basis to identify probable attack vectors.
Develop an AI impact assessment to educate business executives on where investment and implementation makes the most sense. Prepare your platforms for scalability as GenAI use grows.
Work with the CISO on prioritising the security and confidentiality of financial data protection.
Enhance data governance protocols and assess any data privacy risks against privacy laws and regulator guidance.
Collaborate with other risk and compliance teams to guard against improper secondary uses of data and potential legal exposure.

Are companies ready?
Regulatory frameworks are asking companies to swiftly comply with a growing array of requirements. A surge of new regulations — DORA, Cyber Resilience Act, AI Act, CIRCIA, Singapore Cybersecurity Act, etc. — underscores the urgency for organisations to align their practices to these heightened expectations. Addressing these challenges is essential to building a resilient and compliant cybersecurity posture that can withstand both regulatory scrutiny and emerging threats.
Confidence gap: CISOs feel less certain than CEOs about cyber compliance
Despite the belief that cyber regulations are helping the organisation, there’s a significant difference between CEO and CISO/CSO confidence in their ability to comply with these regulations.
The biggest gaps involve compliance with AI, resilience and critical infrastructure requirements. CISOs, who are on the front lines of cybersecurity, are less optimistic than CEOs about their organisation’s ability to meet these regulatory requirements.

Executive call-to-action
Deliver frequent reporting to executive leaders on the state of regulations that directly impact respective industry or territory needs, and work towards implementing technology and regulatory change management processes.
Verify the accuracy, completeness and defensibility of all regulatory disclosures of cyber risk management and program posture. Develop a clear understanding of materiality and the specific impact of a cyber incident, incorporating cyber risk quantification to accurately assess and communicate potential risks.
Understand oversight responsibilities to guide compliance efforts, including any necessary coordination between different business units. Identify key questions to ask CISOs to close any knowledge gaps on compliance posture.
Stay abreast of regulatory compliance requirements and collaborate with the CISO and CRO to incorporate proactive compliance measures and monitoring to periodically confirm compliance.
Determine the right amount of disclosure details needed to fulfill cyber program reporting obligations, striking a balance between transparency and confidentiality.
Stay abreast of emerging regulatory requirements and seek input from management on proactive measures being taken to prepare for new requirements. Understand management’s approach to assessing and disclosing cyber incidents.

Unlocking the potential of cyber risk quantification
As cyber threats rapidly evolve in scope and sophistication, the demand for cyber risk quantification is on the rise. However, despite its widely acknowledged benefits, several challenges persist, among them data quality issues and output reliability .
Measuring cyber risk is critical but limited
Executives largely agree that measuring cyber risk is crucial for prioritising cyber risk investments (88%) and allocating resources to areas of highest risk (87%). However, only 15% of organisations can actually follow up to a significant extent.
Executive call-to-action
Consider starting small with a specific output in mind. Leverage the information you have within your organization (e.g., controls effectiveness, maturity, incident or loss data. New tools can help with risk quantification but aren't a requirement. Define your program and look for enabling technologies to support what you've designed.
Show C-suite executives the most impactful financial risk measurement outcomes from quantification tools and practices. These examples can help persuade leadership to prioritise and allocate the right resources to the highest areas of risk.
Work with your CISO and CRO to gain a deeper understanding of the business value of cyber risk quantification and the potential costs and missed opportunities from not measuring cyber risks.
Understand the methods your organisation currently uses to assess cyber risk. Press management on its plans to implement risk quantification more broadly to better assess and report on the company’s cyber risk posture.

Investing in resilience
Cybersecurity continues to evolve into a critical business priority. Organisations are beginning to see its potential as a key differentiator and a way to enhance their reputation and trustworthiness.
Cyber budgets are growing, with a particular focus on data protection and trust. By strategically investing in these fields, companies are building resilience and positioning themselves favourably in their customers' perception.
Investing in what matters most: Cloud and data trust go hand-in-hand
Over the next 12 months, organisations are prioritising data protection/trust and cloud security above other cyber investments. They understand that securing sensitive information is vital to maintaining stakeholder trust and brand integrity.
Business and tech executives rank a different list of priorities based on areas specific to their roles.
Business executives regard data protection/trust as their top cyber investment priority (48%), followed by tech modernisation and optimisation (43%).
Tech executives continue to focus on cloud security (34%) as they did last year. The next priority is data protection and trust (28%).
Cybersecurity and trust: The new competitive edge
Organisations increasingly view cybersecurity as a key differentiator for a competitive advantage, with 57% of executives citing customer trust and 49% citing brand integrity and loyalty as areas of influence.
As cyber threats escalate, a strong cybersecurity posture isn’t just about protection — it’s about building a reputation that customers and stakeholders can rely on.
Executive call-to-action
Translate the business case for data protection and cloud security investment priorities to CFOs based on the business value of key outcomes (e.g., reducing the time to recover mission-critical data or patching a system).
Determine the business value of data protection and cloud security to gain stakeholder trust and make more informed cybersecurity investment decisions.
Collaborate with tech, security and finance executives to pinpoint the most essential data security and integrity priorities to guide the information and cloud security investment strategy. Confirming data quality and readiness is necessary to increase security investments.

Cyber strategy and leadership
From lagging resilience efforts to gaps in CISO involvement in strategic decisions, there are clear areas where strategic alignment is needed. To get there, organisations should emulate the leading cybersecurity practices of their top performing peers. They should also move beyond addressing known threats and implement an agile, secure-by-design approach to business, one that strives to build trust and lasting resilience.
Partial implementation isn’t enough
Despite mounting concerns about cyber risk, most businesses are struggling to fully implement cyber resilience across core practices. A review of 12 resilience actions across people, processes and technology indicates that 42% or fewer of executives believe their organisations have fully implemented any one of those actions. More concerning, only 2% say all 12 resilience actions have been implemented across their organisation. This leaves a glaring vulnerability — without enterprise-wide resilience, companies remain dangerously exposed to the increasing threats that could compromise the entire operation.
Here are just a few key areas that would benefit from cross-organisational attention.
- Establishing a resilience team (only 34% say this has been implemented across the organisation)
- Developing a cyber recovery playbook for IT-loss scenarios (only 35% say this has been implemented across the organisation)
- Mapping technology dependencies (only 31% say this has been implemented across the organisation)
Elevating the CISO: Aligning strategy with security
Many organisations miss critical opportunities by not fully involving their CISOs in key initiatives. Fewer than half of executives tell us that their CISOs are largely involved in strategic planning for cyber investments, board reporting and overseeing tech deployments. This gap leaves organisations vulnerable to misaligned strategies and weaker security postures.
Executive call-to-action
Make the business case to the rest of the C-suite for why it’s imperative that CISOs be involved in strategy, planning and oversight of the cyber risk mitigation and resilience strategy.
Participate in cyber resilience assessments and exercises to better understand gaps and approaches CISOs might face for integrating leading practices, standards and controls.
Stay informed and educated on cyber risk program developments, especially related to the organisation’s cyber risk and threat exposure, to meet expanding oversight and governance responsibilities.
Bridging the gaps to cyber resilience: The C-suite playbook
Request the full playbook and access more of the latest findings for 2025.
About the survey
The 2025 Global Digital Trust Insights is a survey of 4,042 business and technology leaders conducted in the May through July 2024 period.
A quarter of leaders are from large companies with $5 billion or more in revenues. Respondents operate in a range of industries, including industrials and services (21%), tech, media, telecom (20%), financial services (19%), retail and consumer markets (17%), energy, utilities, and resources (11%), health (7%) and government and public services (4%).
Respondents are based in 77 countries. The regional breakdown is Western Europe (30%), North America (25%), Asia Pacific (18%), Latin America (12%), Central and Eastern Europe (6%), Africa (5%) and Middle East (3%).
The Global Digital Trust Insights Survey had been known as the Global State of Information Security Survey (GSISS). Now in its 27th year, it’s the longest-running annual survey on cybersecurity trends. It’s also the largest survey in the cybersecurity industry and the only one that draws participation from senior business executives, not just security and technology executives.
PwC Research, PwC’s global Centre of Excellence for market research and insight, conducted this survey.
Contact us


Partner, Threat und Incident Management Leader, PwC Austria
Tel: +43 699 163 050 22



